Introducing Cliff's Stand-up Series. Cliff Audinet, Xvouchers VP of Technology, discusses Xvoucher, Technology, Learning and its impact on you.
There’s been a lot of talk, and action, with regards to cyber and information security threats against consumers and businesses. There is a lot of advice out there for both consumers and business. Today, I am going to focus on what it means when you represent a business. Say you’re an individual contributor, a manager, or in the C suite of an SMB or Enterprise organization, what does that mean as far as how you control your information? Well, here comes the cold, hard, truth.

You, the employee, are absolutely responsible for the information that you create, utilize, and distribute, executing the daily tasks and responsibilities of your specific position. You don’t own any of it, the organization that you work for does. In addition, any information that flows across the networks of the organization that you work for is also considered their property. And if that wasn’t bad enough, this has been upheld in the courts, so if you are responsible for compromising that information, a striped suit and steel bars are in your future, or worse, being tried by the court of public opinion on social media.
Why is this? Well, information is linked to an organization’s brand, reputation, intellectual property, and their ability to keep you gainfully employed, and thus tied to market share and revenue growth. In a word, money. As you are more and more becoming the product, it is essential that all information is protected.
There is good news in that there are very specific things that you can do to secure the information that you work with on a daily basis.
First, let’s adjust our mindset regarding who’s behind security and information breaches and theft.
Who’s Behind The Curtain
In the past, hackers, which really isn’t the correct term, were less interested in theft of data or destruction of infrastructure and more about proving a point and spreading a message. The hacker in his/her mom’s basement, or in the back halls of academia, were basically cyber social justice warriors, not criminal organizations, thieves, or state sponsored cyber terrorists. Today, however, it is the criminal organizations, corporate thieves, and state sponsored cyber terrorists that lead the cyber attacks globally. What this means to you is that you are up against some serious cyber firepower. The kind of firepower that most enterprise organizations and sovereign nations have, of late, had difficulty dealing with. Just ask Sony, Equifax, the City of Atlanta, Baltimore, Boeing, Panera, Home Depot and the list goes on.
It can seem overwhelming. So what can you do? In another word, deterrent. Like a locked car, or an alarm system sign in your front yard, there are ways to minimize your cyber footprint. The goal here is to have cyber criminals pass you and your organization up for easier targets, of which, unfortunately, there will be plenty. So let’s get to it!
Devices
In this age of BYOD, it seem tempting to do work on personal devices and do personal stuff on work devices. DON’T!! And why not, you ask?
- Your personal device will not be as secure as your work device, leaving your work more vulnerable to theft or destruction. Yes, your IT organization has undoubtedly put network restrictions in place and reduced your local device privileges but that’s a small price to pay for keeping the information you work with secure.
A note: your IT organization works very hard under sometimes trying conditions to secure the information you work with on a daily basis. Don't ignore there policies or guidance. - Personal information that shows up on your corporate device now belongs to the organization you work for. That means it may get backed up on company infrastructure which if that gets hacked, ends up in the hands of not so nice people.
Divide and conquer. If you keep all of your personal items on your personal device, and your work items on a work device, and one or the other gets hacked, you only lose one side, not both. You may not be able to totally control which side gets hacked, but at least you won’t compromise all data in a single moment of anxiety.
Network Access
OK, you’re not going to like this, but too bad. Do not, under any circumstances, get on a public network, i.e. WiFi, when using your corporate device unrestricted. There are two ways that you can utilize a public network that are more secure.
- VPN - If your organization has set you up with VPN (virtual private network) access to your apps or infrastructure, then you can use your favorite coffee shop WiFi as the VPN tunnel is secure, even if the WiFi network you are on is not. Keep in mind that if you switch to browser based apps that are not inside your VPN environment, those won’t be protected. Also, please be sure no one is looking over your shoulder.
- Personal HotSpots - If you have a late model phone, either iPhone or Android, then you can utilize the personal hotspot capability to bypass unsecured public WiFi. Why? Because that connection goes from your phone to your cell provider, most likely one of the big four. Although cell data connections can be compromised, that is much more complicated to do than hacking your local coffee shop WiFi. Once you create the hotspot, you can connect your corporate device (laptop or tablet) to the hotspot and you’re good to go. In most cases VPN is supported via this type of connection scenario as well. I had to start a build/release pipeline from a very popular coffee chain on I-85 in the middle of almost nowhere South Carolina. Go personal hotspot! Go VPN!
Social Media
The popularity of social media suggests that we are all really lonely, but aside from that, it’s also a platform that needs to be treated with kid gloves with regards to corporate information security.
- Do not post corporate information on any personal social network accounts. This includes what you’re working on, future plans or tasks for your project, direction for the company, or rants about your job, colleagues, supervisor, or company. These accounts are trolled constantly not only by the social media company that hosts your account, but by trolls, spy’s, corporate competitors, and yes, other countries. Granted, they can only easily get what is publicly available from your profile, mostly... Remember, loose lips sink ships-and careers.
- Do not post personal information on your company intranet, company’s social media accounts, or other information distribution networks your company has given you access to. Your personal life should not leak into the company's brand and reputation via these mechanisms and there will be far less leniency for this discrepancy than for item 1.
These two items point to the rule of thumb in the Devices section above: Never mix personal and corporate information.
Information Security-Plan B, C, and D
So what’s else can you do to secure the information you work with on a daily basis? Aside from the suggestions detailed above, there are some basics that can be implemented as habits, kind of like brushing your teeth everyday. Your dentist isn’t lying to you, and neither am I, this an important daily routine!
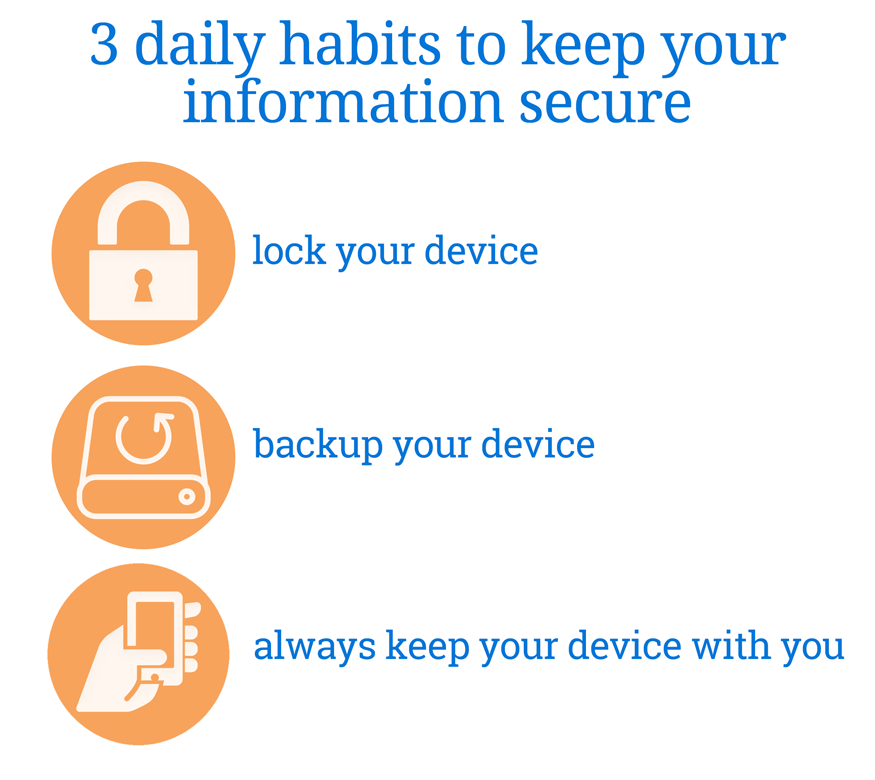
B. LYD - Lock Your Device. Each time you step away from your device, regardless of whether it’s a phone, tablet, or laptop, lock the screen. If it’s a mobile device you’ll need to have the “Require Passcode” option set to “Immediately” (the naming of this item may vary between iOS and Android devices). For Windows laptops it’s the Windows-Key and L. If you’re using a Mac there’s no hot-key so you have to click on the person icon in the upper right and select the Login Window... menu item. Yes, it’s a pain to have to continually unlock your devices, but it’s also a pain to have to explain to your company why information associated with you surfaced online as part of a breach. Not fun...
C. BYD - Backup Your Device. This item goes back decades and has been ignored for as long, or longer. I cannot tell you the number of times schoolmates, co-workers, supervisors, family members, you name it, came cursing and dropping F-Bombs everywhere because they lost their data. A report that took weeks to complete, contact lists, projects, homework, presentations, all gone because something went wrong with the device. And theft or ransomware wasn’t even a thing yet! There are plenty of easy to use local and online backup solutions. Both Windows and Mac have built-in backup features. For Mac it’s Time Machine and covers both files and the OS. For Windows it’s File History and System Image Backup for files and the OS. You just need an external hard drive, or a large enough flash drive and you’re good to go. For online backups you have iCloud for Mac OS and iOS, OneDrive for Windows, and a multitude of third party cloud backup solutions. If your company provides a backup solution use it. If they don’t, see if you can requisition an external drive for your device, for the express purpose of backing up your corporate information. If that device is a phone, sync to it’s home laptop or use a cloud solution, preferably provided by your company.
D. AKYDWY - Always Keep Your Device With You. This seems intuitively obvious, but yet I have seen people walk away from their devices at airports, coffee shops, bars, and restaurants. Sometimes for a short time, sometimes longer. It only takes a few seconds to access a device to install a nefarious application, snap a picture, or just walk away with it. I know it’s not fun to have to pack it all up just to go to the restroom, but it’s also not fun to explain to your company...wait, we’ve been here before...you get the point.
A Final Thought: TLDR
Certainly some of the information security scenarios are similar to your consumer counterpart, just minus the threat of being fired, having your career ruined, or putting your company’s barrier to entry at risk because your device was compromised. Let’s review:
- Hackers have superior firepower, so minimize your cyber footprint so they pass you by.
- Do not mix personal and corporate devices, or personal and corporate information on those devices.
- If you have to use a public WiFi network, be sure to use your company provided VPN or a personal hotspot via your phones cell connection to avoid snooping and hacking.
- Do not mix personal and corporate information on social media platforms. Use only corporate supported social media for corporate information.
- Lock your device, backup your device, and always keep your device with you.
Following these 5 rules of thumb for information security will help to ensure that you minimize your chance of being a victim of cyber crime and mitigate any loss of information on your part .